A penetration testing, colloquially known as a pen test, pentest or ethical hacking, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system. The test is performed to identify both weaknesses (also referred to as vulnerabilities), including the potential for unauthorized parties to gain access to the system’s features and data, as well as strengths, enabling a full risk assessment to be completed.
The goal of this testing is to find all the security vulnerabilities that are present in the system being tested. Vulnerability is the risk that an attacker can disrupt or gain authorized access to the system or any data contained within it. It is also called penetration testing or pen test. Penetration testing typically includes network penetration testing and application security testing as well as controls and processes around the networks and applications, and should occur from both outside the network trying to come in (external testing) and from inside the network. For example this can be a great tool in conjunction with compliance (such as PCI DSS or HIPAA) Risk Assessment to secure all the PII or payment data you store.
The sheer size and scope of the data security industry make it difficult to identify specific risk factors and potential exploitation points. Penetration testing is the perfect way to find the gaps in your current system, with testers trained to think like hackers and stay ahead of the game.
Computer networks are always changing, with services and locations added, new applications introduced, and updates applied as an organization grows and evolves. While it’s important to set up a secure network architecture from the outset, it’s equally important to approach security as an ongoing process that adapts and responds as needed. Penetration testing is not a one-time solution – rather, annual testing is advised and additional tests are needed whenever significant changes are made.
Who performs penetration testing?
It’s best to have a pen test performed by someone with little-to-no prior knowledge of how the system is secured because they may be able to expose blind spots missed by the developers who built the system. For this reason, outside contractors are usually brought in to perform the tests. These contractors are often referred to as ‘ethical hackers’ since they are being hired to hack into a system with permission and for the purpose of increasing security.
Many ethical hackers are experienced developers with advanced degrees and a certification for pen testing. On the other hand, some of the best ethical hackers are self-taught. In fact, some are reformed criminal hackers who now use their expertise to help fix security flaws rather than exploit them. The best candidate to carry out a pen test can vary greatly depending on the target company and what type of pen test they want to initiate.
Penetration testing stages
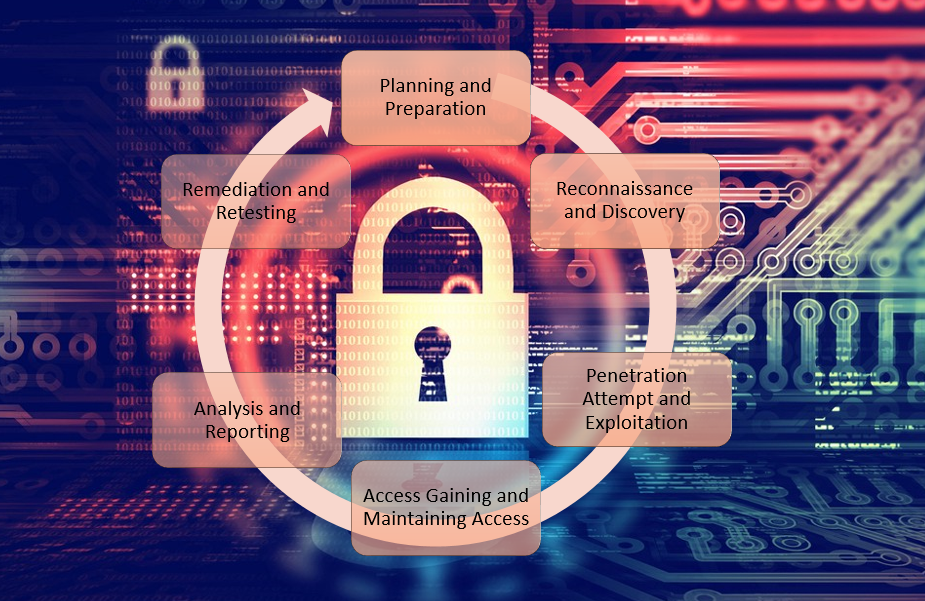
Planning and Preparation
When it comes to penetration testing, planning is indeed the key to success. There are multiple ways to approach a pen test and figuring out your goals and scoping accordingly is key to ensuring that you’re going to get the most out of the process. Consider these questions to ensure your expectations are aligned with the testers and you get the information you’re looking for:
- Do you want an external test, which simulates an attack from an outside individual or organization, or an internal test, which simulates an attack from an insider, or an attacker that has a foothold within the organization?
- Would you prefer your security team to know a pen test is about to be performed, or would you rather it be performed covertly to identify their effectiveness in detecting the activity?
- How much information do you want to share with the pen testers beforehand?
- Where you want to do pen test? Production or staging environment?
- How aggressive are the pen testers allowed to be?
Reconnaissance and Discovery
Once the scope has been established, pen testing teams can get to work. In this discovery phase, teams perform different types of reconnaissance on their target (it can be company or some specified scope or even both). On the technical side, information like IP addresses can help determine information about firewalls and other connections. On the personal side, data as simple as names, job titles, and email addresses can hold great value. Attackers can use this data to send phishing emails or figure out who may have privileged credentials, with which they can get full access to the environment.
Additionally, before exploiting a system, pen testing teams must look for weaknesses within the environment. Often referred to as “footprinting”, this phase of discovery involves gathering as much information about the target systems, networks, and their owners as possible without attempting to penetrate them. An automated scan is one technique that can be used to search for vulnerabilities that can be used as a doorway.
Penetration Attempt and Exploitation
Pen testers can begin using these newly discovered entry points, testing all of the weaknesses they have discovered previously. They will attempt to enter the target through these identified potentially weak entry points. To find all possible security issues, misconfigurations and vulnerabilities penetration testing team runs vulnerability scans against assets in scope. After scanning results obtained pen tester should validate them manually and additionally do manual security testing so in the end he will get as much results as possible and identify most vulnerabilities in tested environment.
Access Gaining, Access Maintenance and Privilege Escalation
Once inside a compromised system, they will try to elevate their access privileges within the environment, allowing them to take any number of additional actions. Gaining administrative privileges enables pen testers to identify security weaknesses in other areas and resources, like poor configuration, unguarded access to sensitive data, or ineffective management of accounts and passwords.
Additionally, multiple types of assets can be tested. In addition to the on-premise network infrastructure and workstations you’d expect could be vulnerable to attack, mobile devices, web applications, and even IoT devices like security cameras, can also be put to the test.
Results Analysis, Validation and Reporting
Pen testers should carefully track everything they do during the discovery and exploitation process. From there, they can create a report that includes all of these details, highlighting what was used to successfully penetrate the system, what security weaknesses were found, and any other pertinent information discovered. These reports should also include analysis to help map out next steps once the test has concluded. Pen testing teams can help determine the highest priority items that an organization should take care of as soon as possible, as well as suggestions for remediation methods.
Clean Up, Remediation and Retest
Just as with a real attack, pen testers can leave “footprints.” It’s critical to go back through systems and remove any artifacts used during the test, since they could be leveraged in the future by someone with nefarious intentions. Once this is completed, an organization can go about the business of fixing the security weaknesses discovered and prioritized during the testing phase. This may include putting compensating controls in place to protect weaknesses that cannot be easily remediated, or even investing in new solutions that can streamline security and improve efficiency.
Penetration tests can and should be utilized frequently, especially when new applications or infrastructure are being deployed. Even if your organization believes they resolved every weakness listed in a previous report, the best way to ensure your remediations are effective is to test again. Additionally, IT environments, and the methods used to attack them, are constantly evolving, so it is to be expected that new weaknesses will emerge.
With so many breaches dominating the news, it’s more critical than ever to reduce the chance that an incident could put your organization’s reputation and trustworthiness at stake. Organizations should do everything they can to understand and avoid behaviors that put them at risk. Pen testing is an essential part of a risk assessment strategy and helps ensure that your organization is reducing the chance of a damaging breach occurring within your environment.

